Advancing Persistently Against APT
Figure 1. Header from a phishing email from Wekby, an APT group. The headers highlighted in blue represent the type of things collected as “indicators”, and in red are the important values.
I’ve had my own personal experiences with APT aka Advanced Persistent Threat. This post is about some of that experience, and a bit of a glimpse down into the rabbit hole including an attack against my own home systems.
Background
First there was the Theater of War, which was a large area where significant military events occur. This Theater included the realms of Land, Sea, and Air. During the Cold War came the Theater of Space. In recent years the term “cyberspace” was used to denote the digital realm, and in conversation this was often referred to as just “cyber” as a form of shorthand, especially during conversations with military personnel to quickly note which realm was being discussed.
The term “Advanced Persistent Threat” was used in the 1990s in reference to small commando groups that troops encountered in Iraq and Afghanistan. They used unconventional TTPs (Tactics, Threats, and Procedures) with little to no direction from commanders except for a general principle of “distract, disrupt, delay, destroy”. The IED (Improvised Explosive Device) is a good example of this mandate in action. In 2006 the US Air Force started using the term APT to describe similarly structured groups in the Theater of Cyberspace, and eventually this was what the term was nearly exclusively associated with. Distract, disrupt, delay, destroy was replaced with information acquisition. TTPs became Tactics, Techniques, and Procedures. These APT actors had the skills to write various tools as needed, some groups were skilled enough to weaponize publicly known exploits and even find and weaponize their own zero days.
I worked for a government contractor as the APT thing really ramped up, and was on a team that dealt with them almost daily. If they gained a foothold and were kicked out, they came back with an improved game. Exploits were fully weaponized and worked nearly 100% reliably. This was an advanced strategy, it was insidiously persistent, and most definitely a threat.
When the term APT came out in public, many in the Infosec community saw this as nothing more than a marketing ploy by software vendors and consulting firms to sell solutions. And truthfully, it was being used like that by some vendors. But still I had colleagues saying things like “you can’t tell it’s China from an IP address” or “it’s hardly advanced, that’s not a zero day”. I was surprised how limited this line of thinking was, although at the time I wasn’t allowed to even comment on it.
So Was It Really China?
The reality was that the front line defenders of APT attackers like myself did not care who the nation state sponsor was. We’d track hundreds of what we called “indicators”. Yes this included IP addresses, but it included dozens of other things as well. For a phishing email, we’d note the sender address, the domain the sender came from, who registered that domain and what the contact’s name and email address were, the source IP address, the general subject, verbiage in the body, attachment or link, type of attachment, the email agent in the header, the recipient and that recipient’s department, the time and day of week it was sent, and so many more. This was just the email - we’d examine the attachment in great detail and note the exploit being used and the chain of events the exploit would trigger. For a web link in an email, we’d note what domain, who registered it and when, what the payload was, and so on.
When you compared these over time, patterns would emerge that would reveal different groups of attackers that easily stood out from the others. By building a library of each group’s TTPs, if you identified a group attacking you, you had a pretty good idea what that group’s next step was.
To address the People’s Republic of China question, during analysis noting that a compiled executable backdoor was compiled on a Chinese language computer with a Chinese language compiler during working hours in China was a good clue they were backed by the PRC. Probably the classified briefings best answered the question as you heard from the Intel community. But based on the data from the hundreds of indicators, we were always right on the guesses as to which group was sponsored by which country. And the real truth was that it didn’t matter. We could detect an attack and had to see if it was successful or not, and if it was we had to contain it and clean things up. When you saw 2-3 a week, you learned to act quickly and develop your own tactical responses.
Example of an attack
I’ve personally seen attacks from a few different APT actors against my home systems, all seemingly directed at me and fellow hackers personally. The fact that NMRC has helped protesting Chinese nationals with technical advice and helped human rights groups that worked on behalf of people living under repressive regimes might have also kept nmrc.org addresses on a few lists as well. But I am certainly not unique in this - a number of Infosec people with ties to government agencies and defense contractors have been targeted at home. I will say it is not nearly as common today as several years, as the last one I saw was five months previous to me writing this (for what it’s worth, I suspect Russia in that one). But here is one I documented halfway decently that helps illustrate the whole approach to APT (see Figure 1 above).
Looking at the body of the email it was clear this was a phish. But what caught my eye was the IP address of the link in the email. It looked familiar. I had a hunch it was APT-18 aka Wekby (see Figure 2).
Figure 2. The entire body of the email. The telltale signs something is wrong are in red, and my notes about it are in blue. All were consistent with Wekby.
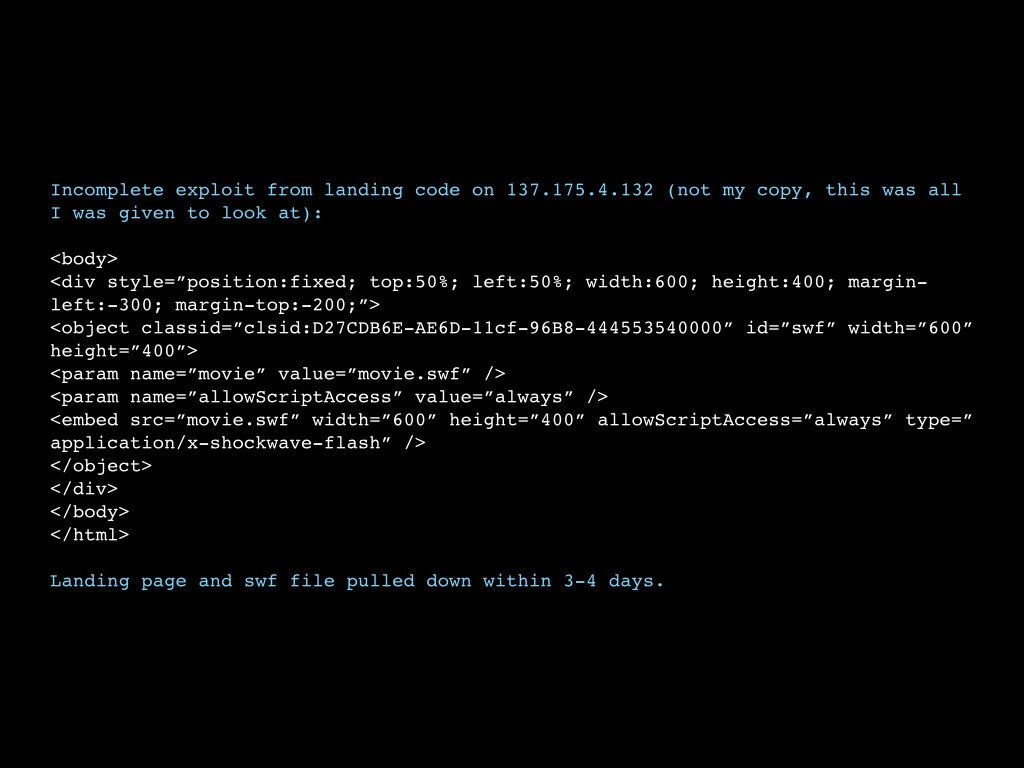
Using an Adobe Flash exploit, a vulnerable swf file was served up (see Figure 3). The vulnerability was exploited to perform one action, a download of a RAT (Remote Access Trojan) associated with Wekby.
Figure 3. I did not think to get a copy of the landing page when I first visited, but a friend at a consulting firm that does incident response and provides information to researchers sent me this. My notes are in blue.
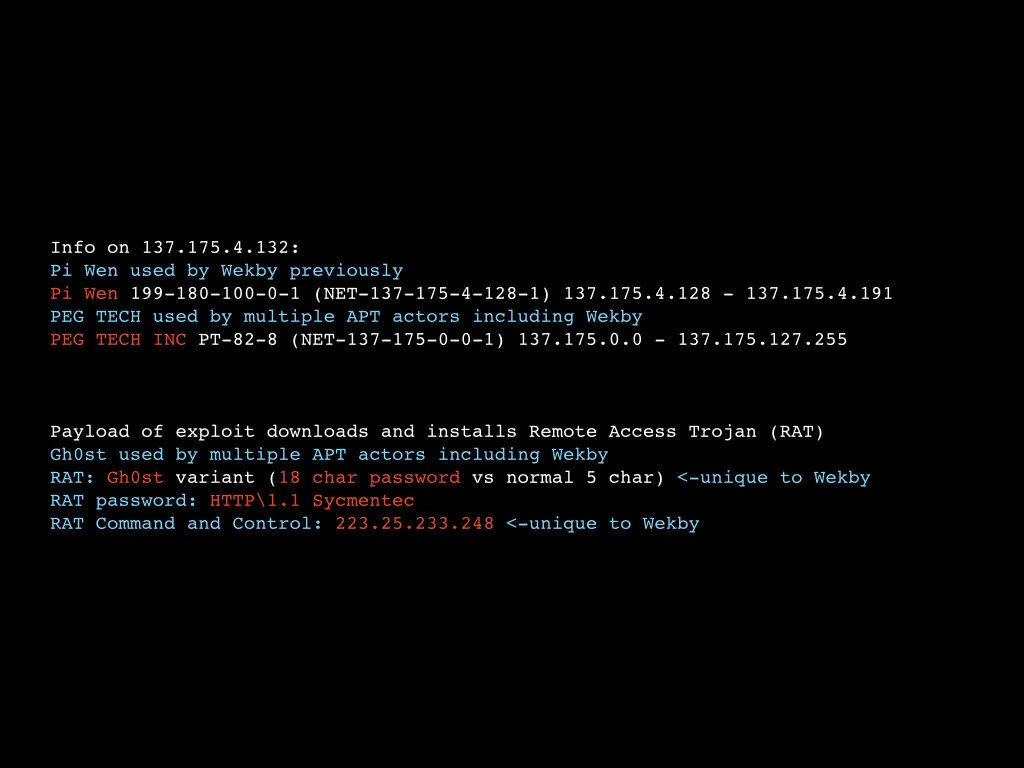
After examining the IP address and the RAT (see Figure 4) I was convinced. Later I checked in with some APT-handling friends who said yes, Wekby.
Figure 4. Part of my notes regarding data collected on the IP address and the RAT. Highlights are in blue, the parts specific to Wekby are in red.
Conclusion
Hopefully this gives you a bit of insight into how APT does its work, a glimpse into using a lot of indicators, and how this whole attribution thing works as well. One of the tools used when I did this at my previous employer was something called CRITs, which is now open source and supports numerous standards including STIX and TAXII, all of which came out of the ranks of dedicated personnel tracking APT. Check it out!
If you collect enough data and organize it effectively, the patterns will emerge and you can see with great accuracy which set of attackers is coming after you. And most importantly, know what their next steps might be.